



Chapter 1
An Overview Of Information Security
In the most well defined terms Information is said to be a well-ordered
collection of data that has been ordered to suit specific ends. The information
that is collected is of utility if it is available to the right person at the
right time. Information may be of little or great importance but every bit of
information that is stored is liable to be infiltrated. Information that is
usually stored in an organizations database may be of one of the following types
:
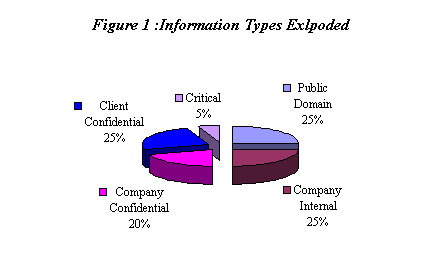
1.
Public Domain Information.
2.
Company Internal Information.
3.
Company Confidential Information.
4.
Client Confidential Information.
5.
Critical information.
Information that is to be made available to the general public is the
information that requires minimum security, nonetheless it is still liable to be
masqueraded and hence does require some amount of protection. This information
may be The website of the company or the information that the PR team of the
company is willing to make Public in order to gain Publicity. This information
is available to the Universe in general.
Company Internal Information is the next higher level of Security that is
warranted, This information generally is meant to be available to the internal
people of the organization this information too is classified and
compartmentalized into access levels and hence needs to have the most discreet
of access control measures for people inside the organization.
Company Confidential Information is the next higher level in the security
ladder. This information usually consists of information related to the smooth
running and the future plans of the company, it may be the kind of information
relating to stocks or relating to the R&D work being carried on in the
organization, the financial status etc. It is the information that is available
to a very few people in the company, like the top management and the owners etc.
Client Confidential information is the kind of information that is of
utmost importance to the company in order to have the faith and trust of their
clients. This is usually the information that the client provides the customers
with under the oath of secrecy and confidentiality which if broken can have
extremely serious consequences to the business. Hence this is the kind of
information that will be of great value to competitors and has to be guarded
with life.
Critical Information is formed by parts of both company confidential and
client confidential information along with some other information such as tax
plans etc. This the most delicate part of all the information that a company
deals with and has to be guarded with the utmost care.
The percentages of the kinds of different forms of information in the
organization are characterized by the Pie Chart shown below.
Information security is the field of securing the information that an
organization possesses and making it available to only the right users at the
right time. Information security is a holistic approach toward securing the
information. It does not deal only with the security of information in digital
form but also the general breach of trust and leak of confidential information.
This may be in the general form as of people giving out information verbally and
in the form of breach of paper communication, which is expected to be
confidential. People may also hand over vital information in casual discussions
etc. Securing the digital information is one of the aspects of information
security which deals with providing restricted and need based access to
information to people. The next major aspect of this digital security is that
which evolves out of the sharing of information, and resources by people by
constituting them into networks, and we meet face to face with the new term of network
security, which becomes more and more demanding with the continuously
burgeoning internet. Adding fuel to the already raging fire of networking and
internetworking, is the way the internet has developed into a great source of
data and even business.
To get full copy of the Report (Free of Cost) please contact Amit at amitgaurs@yahoo.com
